When mobile data, video and streaming plans started offering an “all-you-can-eat” menu, they included just that – unlimited usage. Regardless of the amount of data used, the concept was that the subscriber was charged a single fixed rate each month, in order to avoid overage charges and customers’ experiencing bill shock. Many in the industry believed these flat rate tariffs would alleviate the need for billing and rating validations or requiring assurance services. Instead, what transpired was a realization that the complexities of revenue assurance audits simply shifted the goal posts for revenue assurance teams to continue to deliver billing accuracy.
While it is difficult to imagine that things could get more complex in our industry, the IoT and the next generation networks being deployed that will open the flood gates to an onslaught of new data, have made us scratch our heads once again. A flat rate in the IoT world is not the flat rate that we once knew.
As communication service providers (CSPs) begin to utilize their 5G network investments by launching services, such as IoT, billing vendors and CSP marketing teams will start to roll out new innovative billing models. The monetization opportunities brought on by the IoT bring a fresh approach beyond the standard rating and charging designed for connectivity usage. With 5G, opportunities arise with network slicing, quality of service (QoS), WiFi hotspots, and services provided through multiple service providers. We’ve already seen some examples of innovative business models with various content streaming packages, where different resolution, type and number of shared devices become part of a CSP service bundle.
5G network slicing is an interesting use case that demonstrates the potential for new business models to be applied to IoT. For example, if we take a surveillance camera service provided by a CSP that uses two different network slices - each with different performance and cost characteristics. An Enhanced Mobile Broadband (eMBB) network slice provides low-cost connectivity, suitable for always-on low-resolution access, and uses specific tariffs and units of measurement for charging. When it’s necessary to zoom in on the camera image, users can rely on a high-resolution access, which is provisioned in a more expensive Ultra Reliable Low Latency Communication (URLLC) network slice. This URLLC network slice is configured at a different charging tariff and uses a different unit of measurement for charging.
This particular use case is just one example of many possible scenarios where CSPs can allocate different 5G slices to different services at different billing models and prices. Ultimately these new use cases will lead to defining which devices on a data plan are allowed higher data demands, tracking the levels of network congestion at any given time and offering slower bandwidth options through a variety of competitive pricing models to meet customer demand.
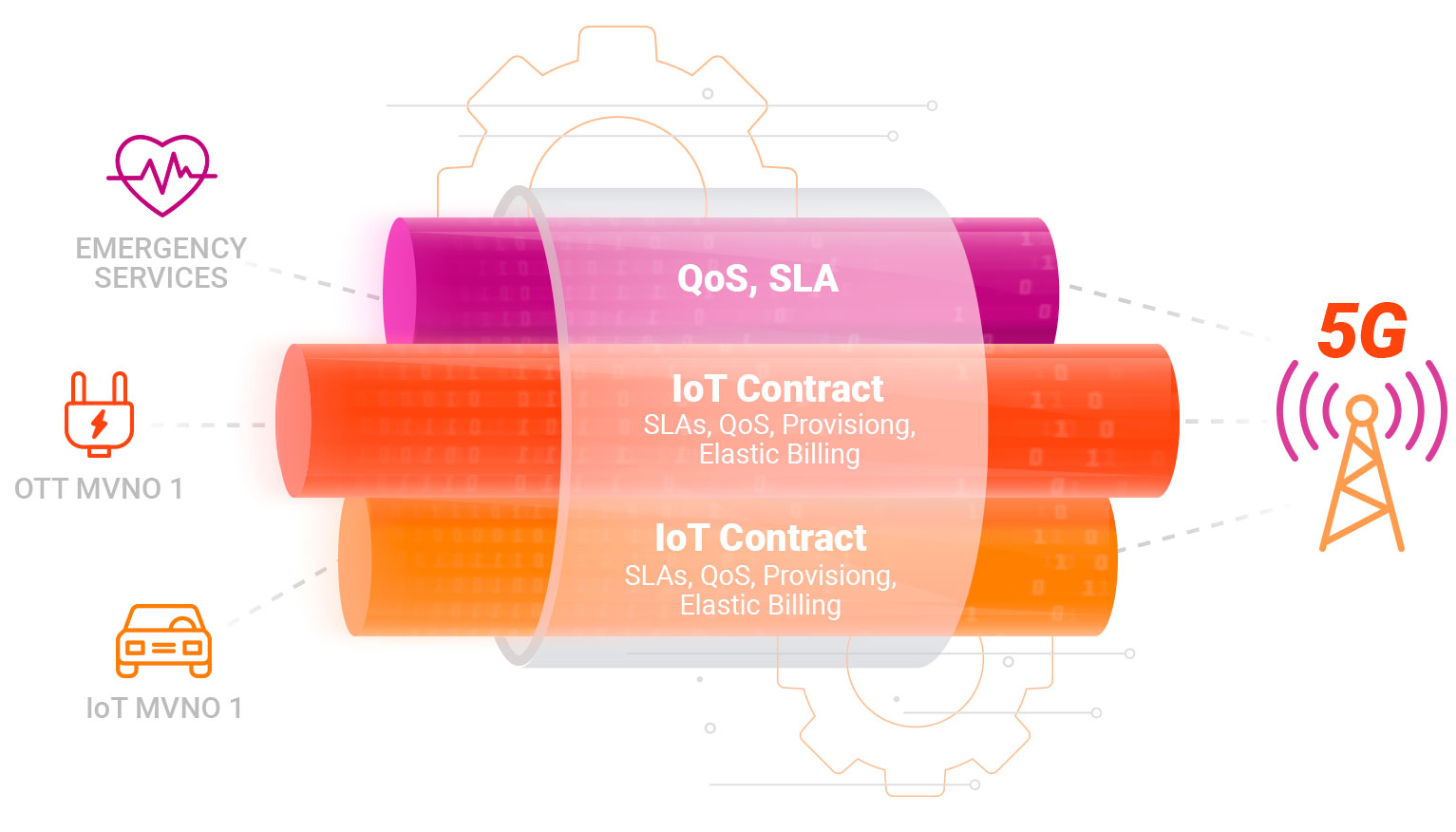
The pace of technological changes introduced by 5G communications is transforming the way networks are built and services are delivered. To stay competitive, CSPs will need to offer flexible and scalable IoT solutions that can be quickly deployed. From a billing and charging perspective, these changes will a put tremendous pressure on CSPs to upgrade their policy and charging solutions in order to not only keep up with the demand that connected devices will generate, but also to monitor and control any potential for revenue leakage.
Where it once seemed that our rate plans might be getting simpler, this next generation of IoT business models, and the endless combination of factors, are shaking things up. The many potential use cases for connecting things to the Internet will require robust risk mitigation methodologies and auditing capabilities for billing and rating validation. This is only possible with the power of advanced analytics and automation, which turns data into powerful risk management insights and actions in order to safeguard against vulnerabilities.
By Carlos Marques, Head of Product Marketing & Analyst Relations, WeDo Technologies





